25+ process flow diagrams are used by which threat model
Defines a domain model and Web Services Restful AtomPub and browser JSON bindings that can be used by applications to work with one or more Content Management repositoriessystems. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency.

Data Flow Diagram Template Mural
The output of a threat modeling exercise is a list of threats - or even.
. It also covers sensors and other devices such as programmable logic controllers which interface with process plant or machinery. The CMIS interface is designed to be layered on top of existing Content Management systems and their existing programmatic interfaces. Organizations with ransomware attacks.
Use tools to draw your diagram If you dont like to manually draw your DFD. The writer researches and then submits your. Facial perception is an individuals understanding and interpretation of the faceHere perception implies the presence of consciousness and hence excludes automated facial recognition systemsAlthough facial recognition is found in other species this article focuses on facial perception in humans.
Business Process Model and Notation BPMN is a standardised diagramming system used to visualise business processes. Time Stops in the Mediterranean Day 07 442 Our time stopper sneaks in on a couple in the shower NonConsentReluctance 082812. Model Lifted Index MLI - the lowest layer in the NWP models is the boundary layer which is 50 mb thick.
In this step Data Flow Diagram should be divided in the context of Model View Controller MVC. 2 This Regulation aims to ensure the smooth functioning of the internal market as regards in vitro diagnostic medical devices taking as a base a high level of protection of health for patients and users and taking into account the small and medium-sized enterprises that are active in this sector. While it is typically used by business analysts and managers its simple and understandable set of shapes and flows makes it a good choice to document.
Week of Jul 04 2021. Time Stops in the Mediterranean Day 09 460. At the same time this Regulation sets high standards of quality and safety for in vitro.
Prominent examples include most vascular plants engaged in mutualistic interactions with mycorrhizae flowering plants being pollinated by animals vascular plants being dispersed by animals and corals with. Be brief in your thought process but remember it must have a logical flow to it. OWASP Threat Dragon The OWASP Threat Dragon project is a cross platform tool that runs on Linux macOS and.
Week of Jul 11 2021. Intro to Threat Modeling. Get 247 customer support help when you place a homework help service order with us.
It is important not to go into too much detail as there will obviously be time constraints involved. This stands for Process for Attack Simulation and Threat Analysis a seven-step risk-centric methodology. System owners can then incorporate these threat events into their cybersecurity risk assessment to develop and prioritise effective controls.
After filling out the order form you fill in the sign up details. Data security and privacy. In terms of the latter point explain to the recruiter how your thought process on the steps you would take to conduct a threat-hunting investigation.
We are the first place to look when you need actionable data to make confident business decisions. Week of Jun 20. We also accept payment through.
It offers a dynamic threat identification enumeration and scoring process. There are several tools available that could be used. The perception of facial features is an important part of social cognition.
Kijk hier voor meer informatie over de status van de nieuwe functies en updates. After paying the order is assigned to the most qualified writer in that field. Once experts create a detailed analysis of identified threats developers can develop an asset-centric mitigation strategy by analyzing the application through an.
Threat Modeling is a pro-active and iterative approach for identifying security issues and reducing risk. Threat Modeling can be defined as the process of building and analyzing representations of a system to highlight concerns about security characteristics. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
We accept payment from your credit or debit cards. They generally arise from. We accept payment through PayPal and debit or credit cards.
It is acceptable in most countries and thus making it the most effective payment method. BPMN diagrams are a form of flowchart similar to UML activity diagrams. Trust your business decisions.
In Microsoft 365 Roadmap wordt aangegeven welke updates momenteel zijn gepland voor de relevante abonnees. Latest breaking news including politics crime and celebrity. PayPal is one of the most widely used money transfer method in the world.
Find stories updates and expert opinion. A leaf plural leaves is any of the principal appendages of a vascular plant stem usually borne laterally aboveground and specialized for photosynthesisLeaves are collectively called foliage as in autumn foliage while the leaves stem flower and fruit collectively form the shoot system. Week of Jul 25 2021.
Week of Jun 27 2021. The misconceptions themselves are implied rather than stated. Ultimately this exercise aims to cultivate a customised threat perspective in system owners.
Each entry on this list of common misconceptions is worded as a correction. You can now pay for your order. Secureworks researchers said a new Iranian state-sponsored threat group is melding government and financial interests by targeting US.
Then the parcel is lifted dry-adiabatically to saturation and moist adiabatically to 500 mb. Mutualism describes the ecological interaction between two or more species where each species has a net benefit. Examples for individuals and groups to adopt to derive a robust system threat model and relevant threat events.
Insider Intelligence maximizes your return on information by providing expert analysis and insights. Week of Jul 18 2021. A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other.
An interview with Rolling Stone founder Jann Wenner about the end of the magazine era not reading Rolling Stone anymore how his son Gus saved it and more The Rolling Stone founder talks about LSD not reading the magazine anymore and how the Stones now look like Lord of the Rings characters onstage. A common misconception is a viewpoint or factoid that is often accepted as true but which is actually false. The mean temperature and relative humidity are used to determine the temperature and dewpoint of the parcel at 25 mb above the surface.
Risk management is the identification evaluation and prioritization of risks defined in ISO 31000 as the effect of uncertainty on objectives followed by coordinated and economical application of resources to minimize monitor and control the probability or impact of unfortunate events or to maximize the realization of opportunities. Risks can come from various sources including. This details will be used by our support team to contact you.
These entries are concise summaries of the main subject articles which can be consulted for more detail. In most leaves the primary photosynthetic tissue is the palisade mesophyll and is located on the. Time Stops in the Mediterranean Day 08 470 A holiday of sun sea and of course sex out of time.
Supervisory control and data acquisition SCADA is a control system architecture comprising computers networked data communications and graphical user interfaces for high-level supervision of machines and processes. Mutualism is a common type of ecological interaction.
Flow Chart Examples 56 In Ms Word Pages Google Docs Pdf Examples
The Anderson Technologies Approach Anderson Technologies

Extending The Zero Trust Architecture Concept To Apis Vmware Security Blog Vmware

Process Flowchart Template Mural
Adonis Simpler And Smarter Features For Better Bpm

Flow Chart Examples 56 In Ms Word Pages Google Docs Pdf Examples

Plantilla De Organigrama De La Corporacion Vector Premium Organigrama Diseno Web Diseno Corporativo
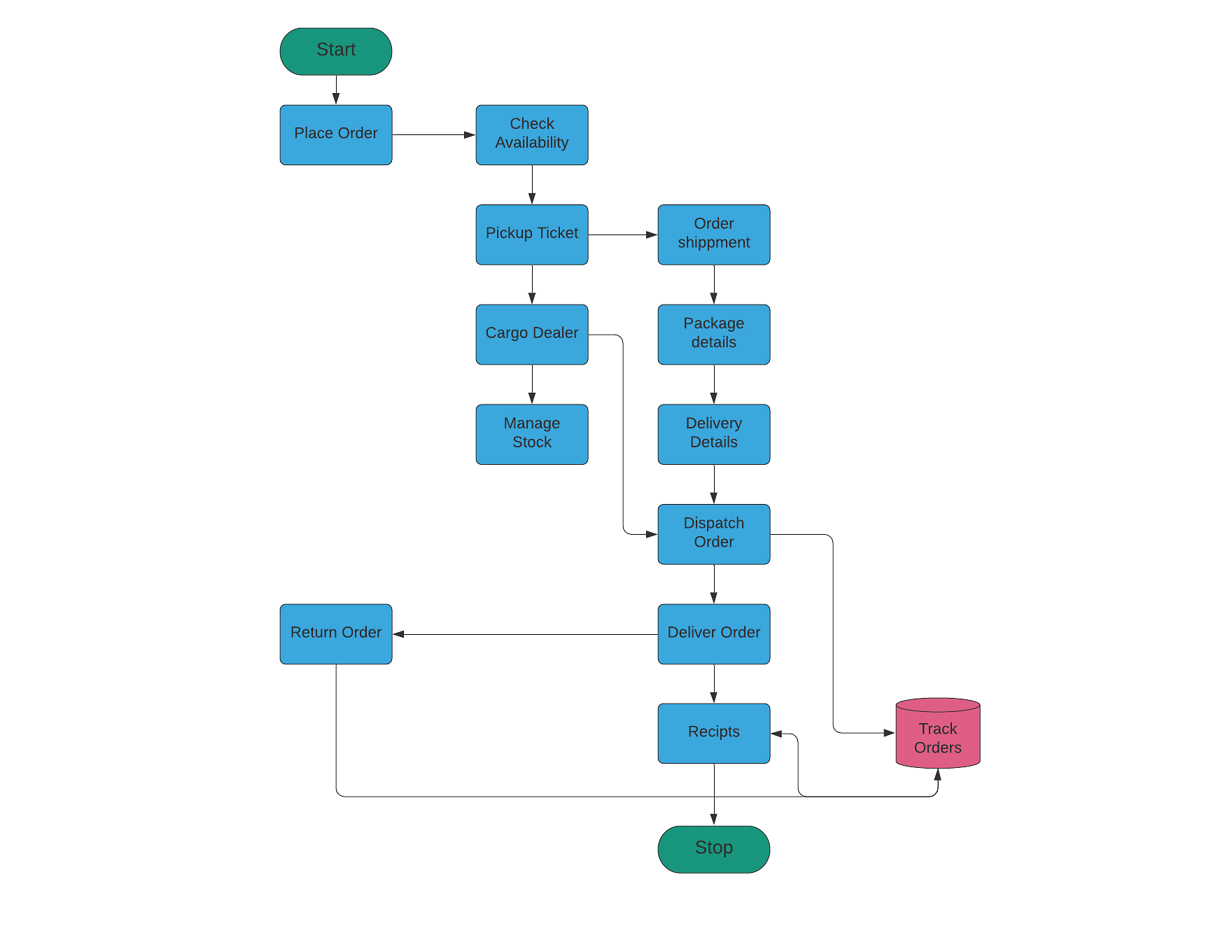
Top 25 Java Projects For Beginners In 2022

Top 25 Microservices Interview Questions And Answers

Sop Templates 15 Standard Operating Procedure Standard Operating Procedure Template Procedural Writing

Business Process Model Diagram Bpmn Template Mural
Flow Chart Examples 56 In Ms Word Pages Google Docs Pdf Examples

Chart 25 Examples Format Pdf Examples

Data Flow Diagram Template Mural
Flow Chart Examples 56 In Ms Word Pages Google Docs Pdf Examples

Piezoelectric Sensor Pinout Working Datasheet Electronic Circuit Design Sensor Electronics Projects Diy
.webp)
J7dx0zzyrnsham